So basically im trying to understand how memory reading works.
Before joining the forum i was already learning c++ and reading some books/forums(unknowncheats) and i have basic knowledge of how it works.
But everything i read till now uses a memory scanner to get pointers/ base address etc.
In those guides you are finding UI elements by ctypes of python not by reading Memory Offsets
For example in other games i see, they usually search offsets with cheat engine and after that in the code they read those offsets, getting values in memory that they can read or edit.
class offsets
{
public:
__int32 LocalPlayer;
__int32 BaseAddress = 0x400000;
__int32 OffsetLocalPlayer = 0x10F4F4;
WORD m_Ammo = 0x0150;
}offsets;
But here you are not doing this, i tried to understand whats going on in the code(i know java, python and c++ , this last just a little started some weeks ago)
And Its unfamiliar to me cause i dont see any static offsets etc.
So if someone can explain to me or point me how to for example read memory or get UI element position, i would aprecciate.
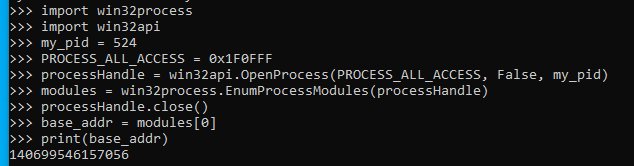
I have done this quickly, basically for get base eve addres with just the pid. But i still dont see how you read memory from specific UI element or how you tell the code to read this element or that. Also i used ELM Debugger, i think i would find eve static offsets there, but i dont, and i dont get what information for there can help my code to read memory.
import win32process
import win32api
# first get pid, see the 32-bit solution
my_pid = 17024
PROCESS_ALL_ACCESS = 0x1F0FFF
processHandle = win32api.OpenProcess(PROCESS_ALL_ACCESS, False, my_pid)
modules = win32process.EnumProcessModules(processHandle)
processHandle.close()
base_addr = modules[0]
With this i have pid and base addres, with those 2 i can start reading from procces memory.
Sorry for big post but i want to read memory myself and i need help in:
1-How to actuall get UI tree and navigate under elements.
2-How elm debugger can help in that.